Configure Permissions and IAM Role
Configure Sudo Permissions for GitLab Runner
GitLab Runner needs sudo privileges to execute CI/CD tasks such as build, test, and deploy. This section will guide you through configuring sudo permissions for GitLab Runner.
- Open Sudo Configuration File
Execute the command:
sudo visudo
- Update Sudo Permissions
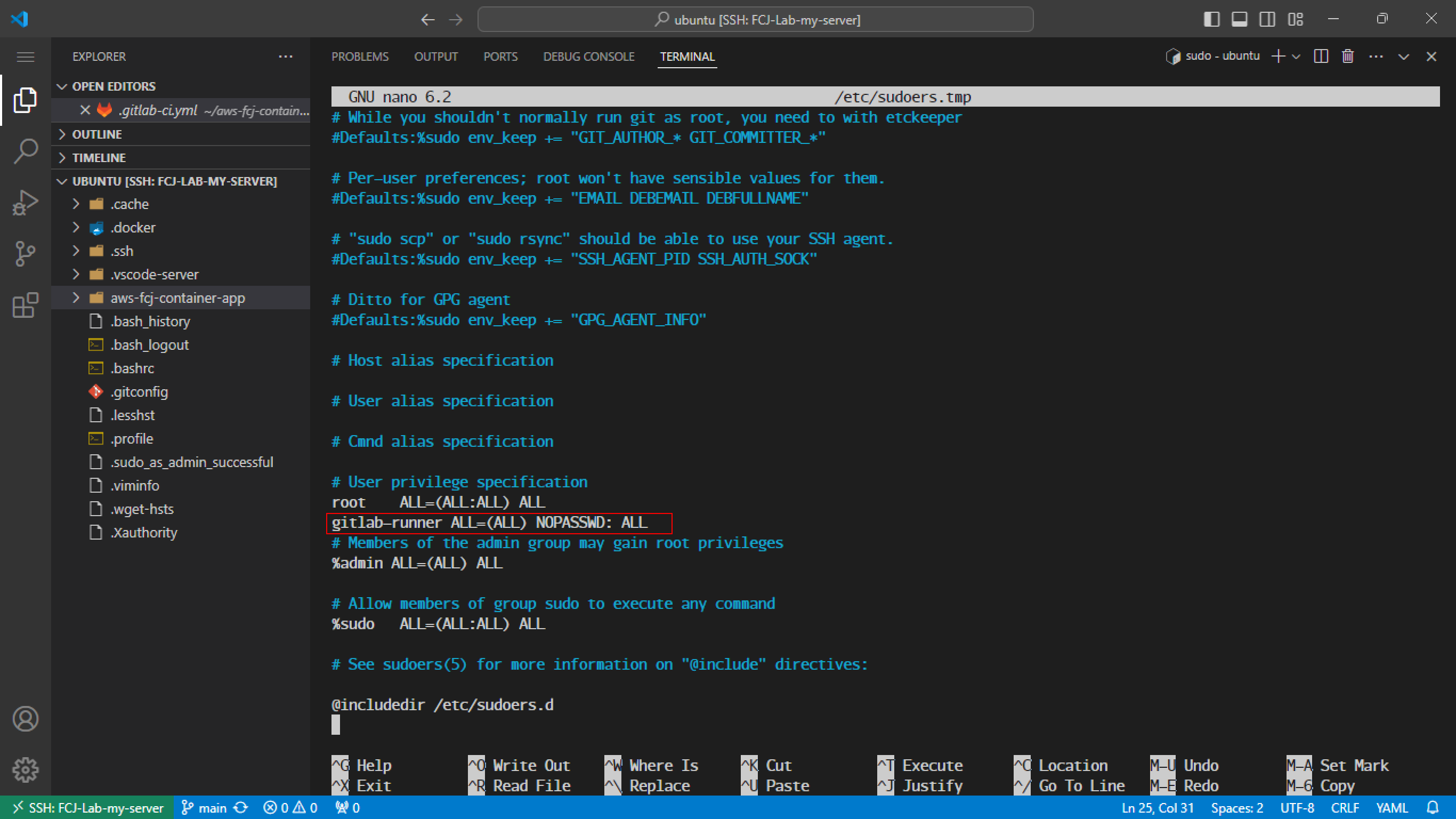
Add the following line to the file:
gitlab-runner ALL=(ALL) NOPASSWD:ALL
After adding, press Ctrl + X to exit, Y to confirm saving, and Enter to complete.
Configure IAM Role
- Access EC2 Instance
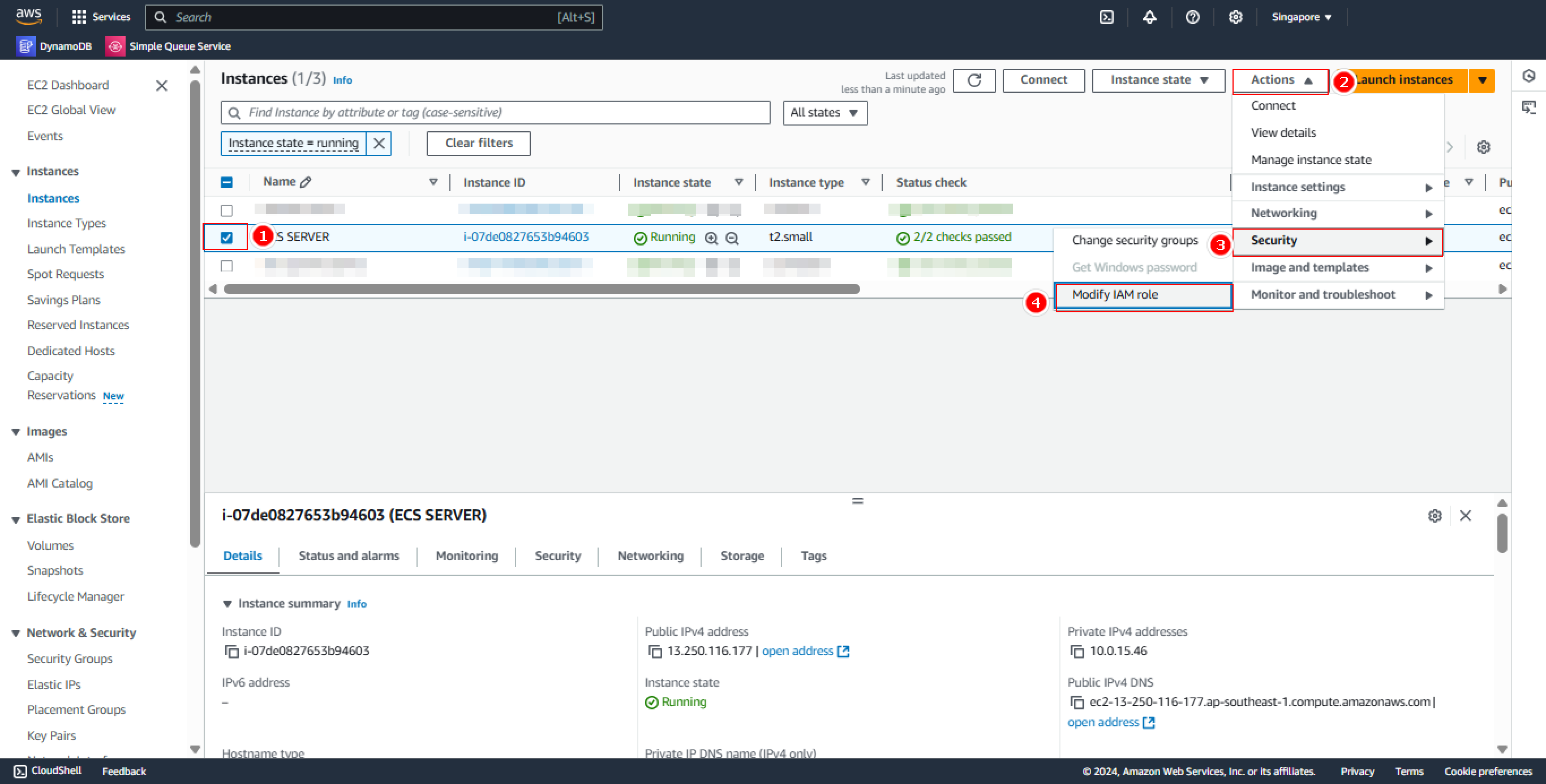
Steps to follow:
- Open EC2 Console
- Select the running instance
- Go to Security tab
- Choose Modify IAM role
- Check Current Role
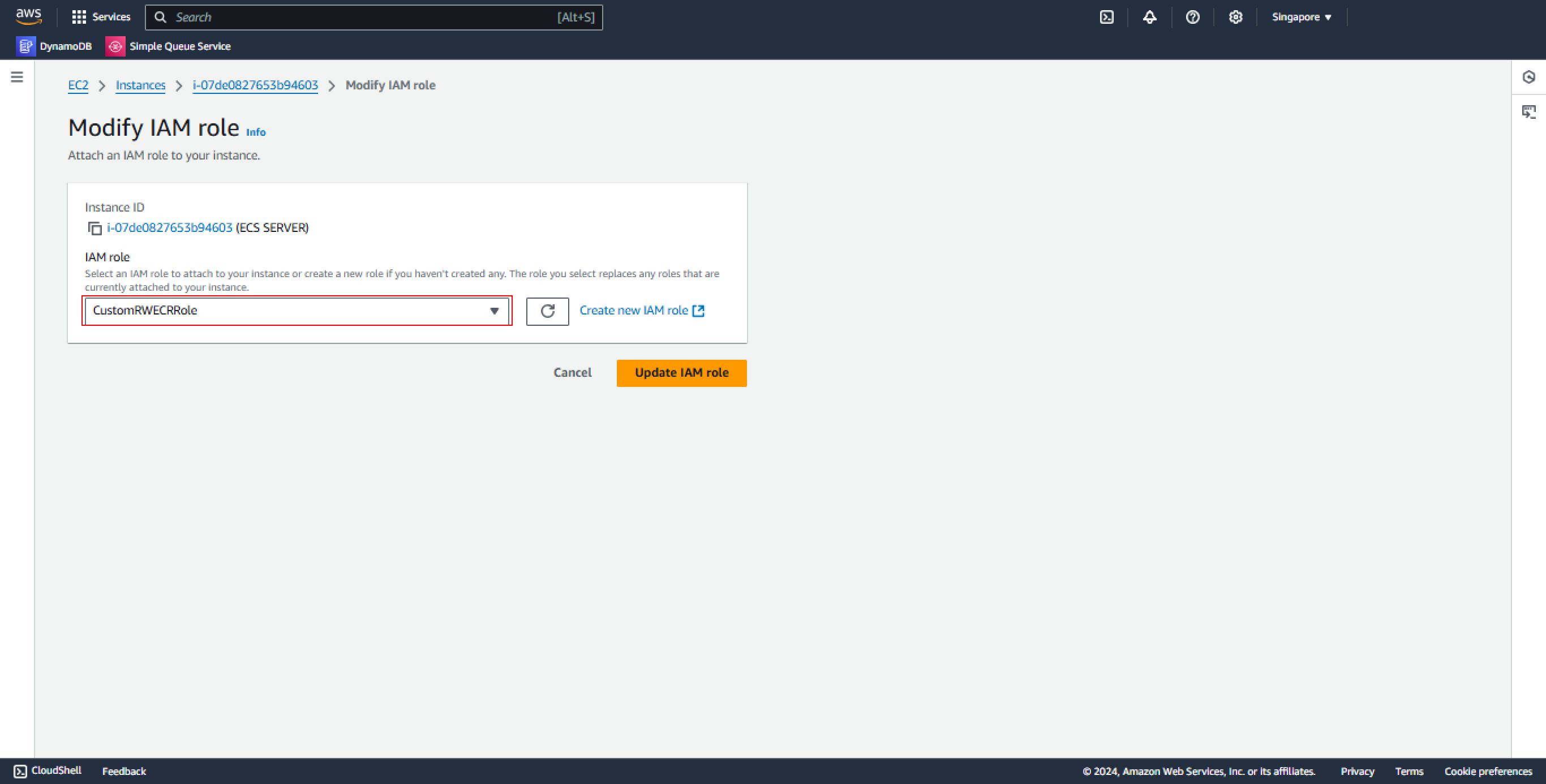
Verify that the CustomRWECRRole IAM Role is assigned to the EC2.
- Access IAM Role
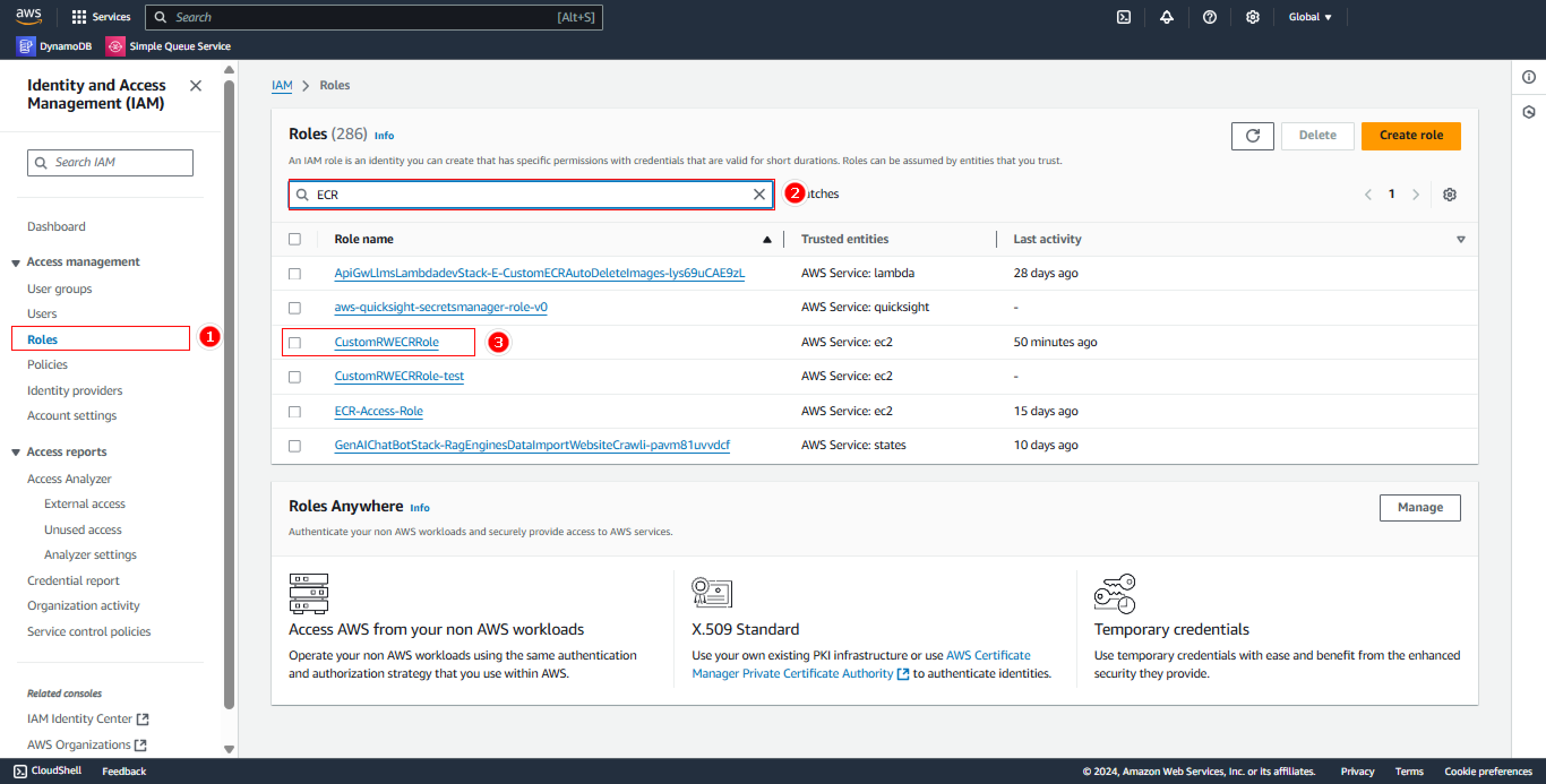
Navigate in IAM Console:
- Select Roles tab
- Find
CustomRWECRRole - Click on the role to view details
- Add Policy
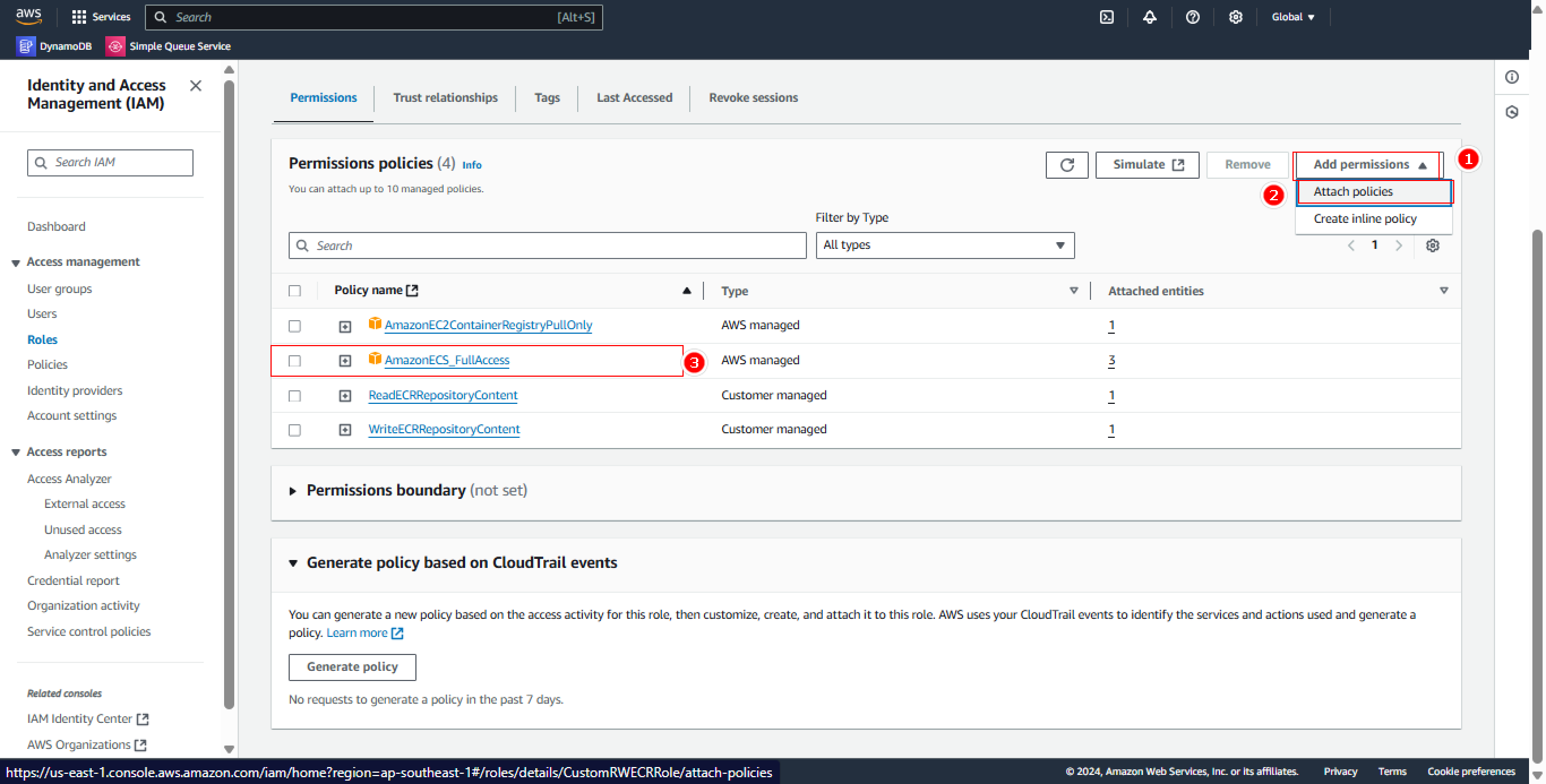
Add new permissions:
- Policy to add:
AmazonEC2FullAccess - Attach to
CustomRWECRRole
Assigning AmazonEC2FullAccess should be carefully considered in a production environment. Follow the principle of least privilege and only grant necessary permissions.